Internet domain gomelbest.info and the mailbox gomel.best@yandex.ru were involved in the hacker attack on state institutions and facilities of Ukraine’s infrastructure.
In March 2017, the Ukrainian team of experts on cyber security Cys Centrum published the report called “Targeted attacks on enterprises of Ukraine using Ursnif harmful programs.” The report showed that on March 14, there were recorded waves of targeted attacks, which resulted in failures of river and sea transport enterprises.
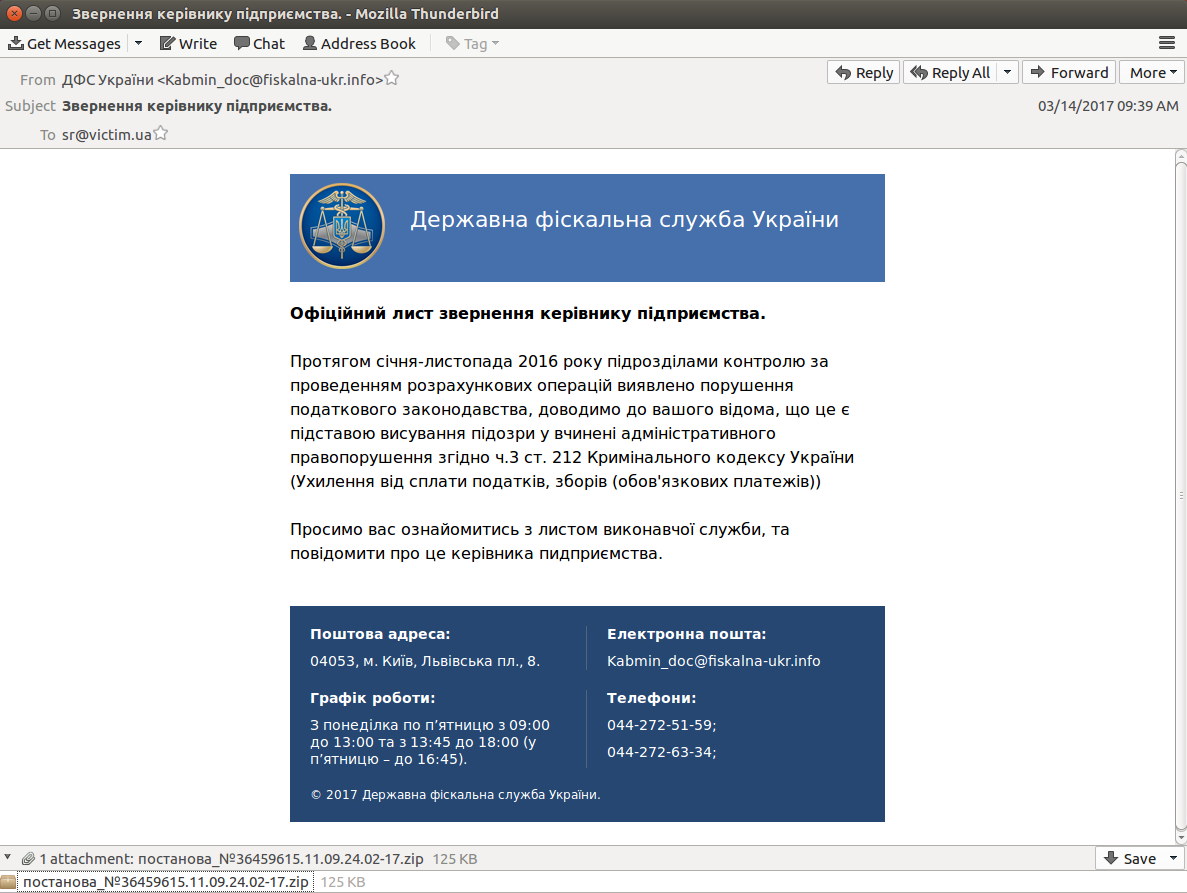
The perpetrators used a conventional email service. Victims received letters allegedly from the State Tax Service of Ukraine coming from different mailboxes. Cys Centrum experts believe that they served as the “bait” and caused people to open a letter with the document attached. Once the user opened it, malware prompted them to activate content (run a macros), and after the activation the built-in malicious code ran itself.
Next, the computer downloaded the Ursnif program. Ursnif functions include remote execution of various commands, information and personal data theft.
At the end of the report experts gave a partial list of the sites and email-address assigned to them in one way or another related to cyber attacks. Most of them are registered in Russia. But gomelbest.info is also on the list.
It recently became known that the gomelbest.info site is operated directly by the KGB directorate of Homiel region. The info came from the ex-secret service agent Syarhei Vasilyeu, who administered the site for nearly 9 years, he now lives in Poland.
According to Vasilyeu, after leaving to Poland, he turned the site off, but the KGB made a mirror and the website continues to operate.
We asked Vasilyeu, is it possible that the KGB controlled site and mailbox were hacked and only then were used for an attack.
“The British company VPS.NET, which sold us a server assumes responsibility of keeping track of all attempts to hack its customers. If such an attempt is discovered, it is urgently blocked. By this standard work all similar companies from Europe and US. During my time as administrator, I was never hacked. The site was always very well protected. I do not know why the KGB would need to do it all,” said Vasilyeu.
We asked for comments the representative of CyS Centrum for comment, he talked to the journalist on condition of anonymity.
“We do not set the task to link the attack and those who are behind it. Public accusations are not our style. Our team of experts focus on how to raise the level of awareness of citizens and organizations of cyber threats and develop countermeasures. But we do know our “cyber-enemies” and appreciate them adequately. Even if specific harmful emails originated in another mailbox, the mailbox is in the same infrastructure that the site you are talking about. In simple words, they should have hidden their actions better,” said the expert.
Recently, Ukraine has repeatedly accused Russia of hacker attacks. In May, Reuters wrote that Russian hackers are suspected in the attack on the power grid of the Baltic States and Ukraine. And on May 16th, cyber criminals from Russia attacked the website of the President Poroshenko’s administration, Deputy Chairman of the department Dmitry Shymkiv said. He stressed that the attack cames from “Vkontate” and “Yandex”.
Belarus was not seen as part of high-profile cyber attacks earlier.
“Belsat” has sent a formal request to the Security Service of Ukraine and is waiting for a response about the role of gomelbest.info in this attack.
Katsyaryna Andreyeva, belsat.eu